In order to have a policy that will authenticate users when they attempt to access the Internet through WinGate, you will need to create the policy based on a request oriented type of event (e.g. ConnectRequest, ProxyRequest, ServerRequest, or Request). These types of events will make available a Result policy item that has an Auth option which will can be used to force users to authenticate themselves to WinGate.
When a user has authenticated themselves with WinGate, they will be placed for the duration of their Internet session, into a special Policy system group known as Authenticated Users.
When a user makes a connection, you can use the User/Group check policy item to see if the user is a member of this special group. If the user is not a member (i.e. they are not currently authenticated) then the policy processing can be directed to a Result policy item that will force the user to authenticate themselves as shown in the policy flow chart example below.
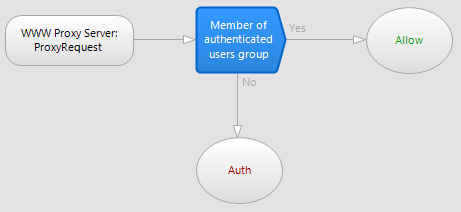
In this example when a user makes a server request to the WWW Proxy server (the event) the policy will the User/Group check policy item (Member of the Authenticated users group) to see if the user is a member of the Authenticated users group. If they are the policy will follow the Yes processing path to the Allow result item.
If they are not a member ( i.e. either they haven't previously been authenticated, or their authenticated session has expired) then the policy will take the No path to the Auth result, forcing them to authenticate with WinGate. Usually clients will be prompted by their browser to enter valid credentials.
(Please refer to the Policy help for information about creating and configuring policies. This step by step will create the policy flowchart shown above.)
You can configure the policy to do more then just processing the Allow result if the user is found to be a member of the Authenticated users group. This could include processing other policy items that make decisions about what the authenticated user is allowed to request, where they are allowed to go on the Internet etc.
©2012 Qbik New Zealand Limited
no comments yet...
You can use basic Full-Text Searches against the page title and body to find matching articles. Use the following search modifiers to refine your query:
You can create a new account or reset your password at forum.wingate.com.
